Le lun. 23 déc. 2024 à 15:37, exploit dev <exploitdevvv@gmail.com> a écrit :
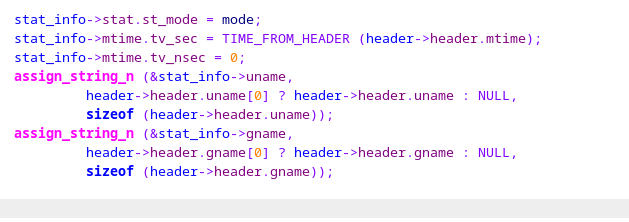
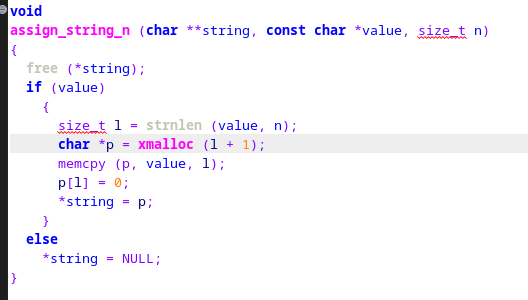
Hello,In decode_header(), assign_string_n() takes input from header.uname as value and also as size_t.If value and n are both controlled, the "l" variable is prone to overflowing inside the xmalloc(l+1)which will under-allocate p, and over-copy value into it.